With business growth, IT security takes a pivotal role in protecting your data, infrastructure, and money flows. Small and medium businesses tend to forget the importance of it, or, more often, they do not have enough physical and human resources to take care of the security issues. That’s where outsourcing of your IT security comes to the stage. Here are some of the most crucial steps for your business IT infrastructure security. You can count on ITAF as your security partner to cover it all.
1# Security patching
Cyber security is an increasingly popular topic. Companies struggle with mail intrusions, malicious emails, data loss. Each business requires preparing for what is coming, such as the new generation of cyber-attacks and AI malware.
Security patching is a level of protection that automates the installment of patches both on a server and individual device levels.
Server security patching
Any server consists of several apps your business uses – from browsers to text editors and more complex tools. Each of that software is prone to having small errors and bugs in it, and software developing companies are frequently producing updates and patches to make tools better.
Any bug in the software, big or small, can be used by a malicious intruder to infest the specific app with the virus or to harm your IT environment.
Delaying the updating of the apps enhances the risk that someone can intrude on your business server, take it over, steal or destroy your data.
Server security patching ensures that the security patches of each software component are installed on time. App providers acknowledge that there is a fault in their software, and they regularly provide patches. However, these patches are not being installed automatically. Someone needs to make sure they are installed regularly. If your company lacks the human resources to conduct it, it may resolve in delaying the patch installing and having a complete infrastructure at risk.
ITAF is a security partner that is regularly checking for available security patches and installing them.
Desktop security patching
Patches are not available and needed only on the server level but also individual device levels. Desktops the individuals in your organization are using are mutually connected as well as being connected to your server, so any harm on an individual device may damage your whole IT environment and endanger the security of sensitive data. That’s why desktop security is one of the pivotal levels of security.
Although patches are regularly provided by software developers, individual users typically just postpone updates on their computers. They are asked to install updates, and in some cases, they do not understand the importance of it and delay the process. This kind of delay may give more time for intruders to infest your network with malware. A bad file on a bad moment on a computer that is not regularly updated can make an organization-level issue.
That’s why ITAF as an IT partner checks for updates regularly so that the individual user does not have to do anything. They only need to restart the machine so that the patches are applied. Software vendor provides a fix – desktop security patching as a service makes sure that the patches are installed in the background.
2# Intrusion detection systems
Having an intrusion detection system is one of the most important precaution steps you can take to prevent your IT infrastructure from intruders.
This service provides monitoring, analysing, detecting the intrusions, and protecting your IT network.
After it detects the attacks, it immediately alerts you and takes the necessary steps to stop the malicious processes as soon as possible.
Host intrusion detection systems (HIDS) and network intrusion detection systems (NIDS) are two methods through which ITAF network specialists gather and analyse information from a computer, server, or network. The goal of these actions is to identify possible threats posed by hackers and crackers inside or outside the organization. Both systems have their advantages and limitations. The best solution is having a combination of both technologies.
Network intrusion system
No matter how protected your business network might be, intruders may always try to get into your system and steal your data. Firewall (to be explained further in the text) presents one layer of protection that stops all kinds of malicious traffic from your network. A network intrusion system is another layer of protection that can recognize an attempt of an intruder to enter your network.
If any service which is a part of your network requires credentials for users to get in, intruders may try to guess these credentials. Someone who wants to guess someone’s credentials can start guessing or even use a tool that runs a script for guessing someone’s credentials every 10 seconds. If there are too many guesses, the intrusion system detects it as suspicious, it alerts the system administrator – that someone is possibly trying to steal your data. This kind of alert calls for checking suspicious behaviour and preventing it.
With a network intrusion system, you are creating a filter layer that is controlling what comes in and what comes out.
Host intrusion detection system
When it comes to host-level intrusions, the detection system is monitoring the devices such as computers. If a computer is linked to a wider network or server, cash register, etc – someone can try to misuse it to approach the server.
An intruder may try typing passwords on the device to enter the databases with sensitive data, or entering USB devices with software trying to take over a computer, trying to execute software that should not be executed, etc. They can try to harm your system with viruses, such as Cryptolocker – a kind of virus that can delete some of the data from the device and the user may not notice it on time.
Host intrusion detection system is based on a small component running on a server detecting inputs and outputs – and checking whether they are malicious. It can also detect if something is removed or replaced with something suspicious. Anti-threat applications, antiviruses, and spyware-detection programs should be installed on every network computer with access to the Internet.
3# Mail anti-virus, anti-phishing, and anti-spam protection
Mails from different servers are going back and forward across the internet – anyone can send you an email. That is why mailboxes are so vulnerable when it comes to malicious attacks, such as phishing and ransomware.
Phishing is social engineering attack used to steal user or company data through stealing login credentials or credit card numbers. It often happens when a malicious mail sender is presenting themselves as a trusted entity (such as a bank). These kinds of emails are asking for login credentials and are mimicking the banks or organizations to deceive people and steal their data.
ITAF offers mail license, mailbox backup, and multifactor authentication, but is also providing mail anti-virus, anti-phishing and anti-spam protection to its customers. This kind of protection provides various kinds of filters that are protecting your mailbox from any kind of malicious sources. This way, your company data security does not depend solely on a human factor and the security awareness of your employees.
Find out why do you need email protection in our detailed article.
4# Secure disk wiping
Each server contains multiple hard drives filled with data. Through time, hard drives can be broken, damaged, or out of support. When this happens, you might need a server replacement. ITAF is making sure all your data is migrated to the new hard disks on the new server, and that the data on old hard disks are securely wiped, before being brought to recycling companies to be disposed of.
Disk wiping is a complex process. Each hard disk from the server must be removed and formatted. When you delete data from the hard disk even though they are not visible, they still exist in another layer. This may bring a risk to data security. Data must be re-written with new values to consider it fully wiped.
As a part of ITAF security services, disks are removed from the server, put in a machine that removes and overwrites it many times so that it is sure that all data are removed from the disk. This procedure is based on internationally recognized data destruction standards.
5# IT Audit
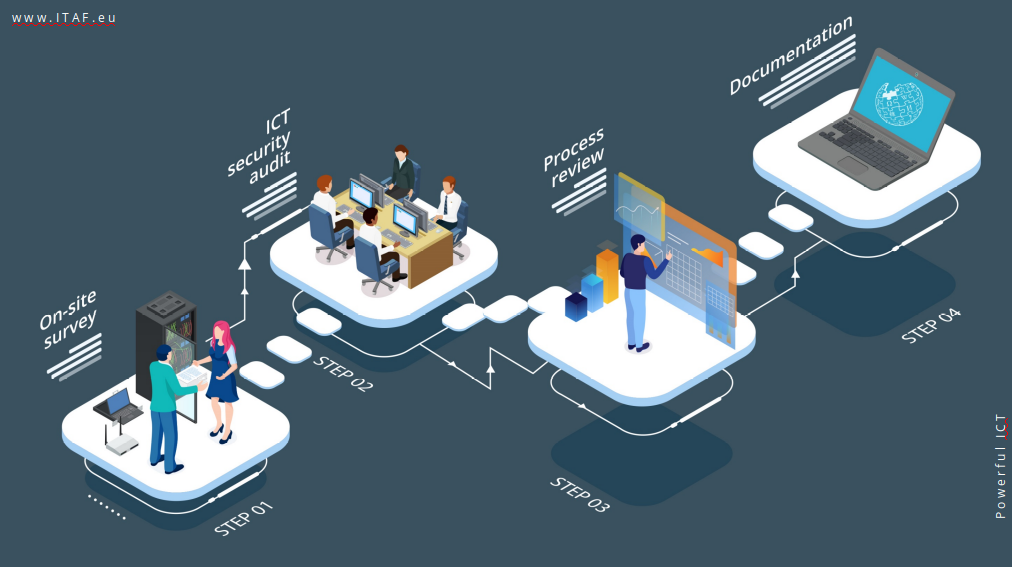
IT Audit is a part of a holistic approach to IT security. ITAF provides an audit of full business infrastructure. This means an audit of all segments of the customer premises – from physical to ICT.
When it comes to physical audits, ITAF is performing a revision of server rooms security, security cameras coverage, parking lot, entrance door – in order to gather information on who can access the building or server rooms.
ICT audit gathers information on who can access the server and data, if everything is security patched, is each employee security trained, do they recognize spam.
Based on gathered pieces of information, the customer receives an advisory document that consists of risks they need to focus on. This focuses on the pain points of customer security environments.
6# Secure connections
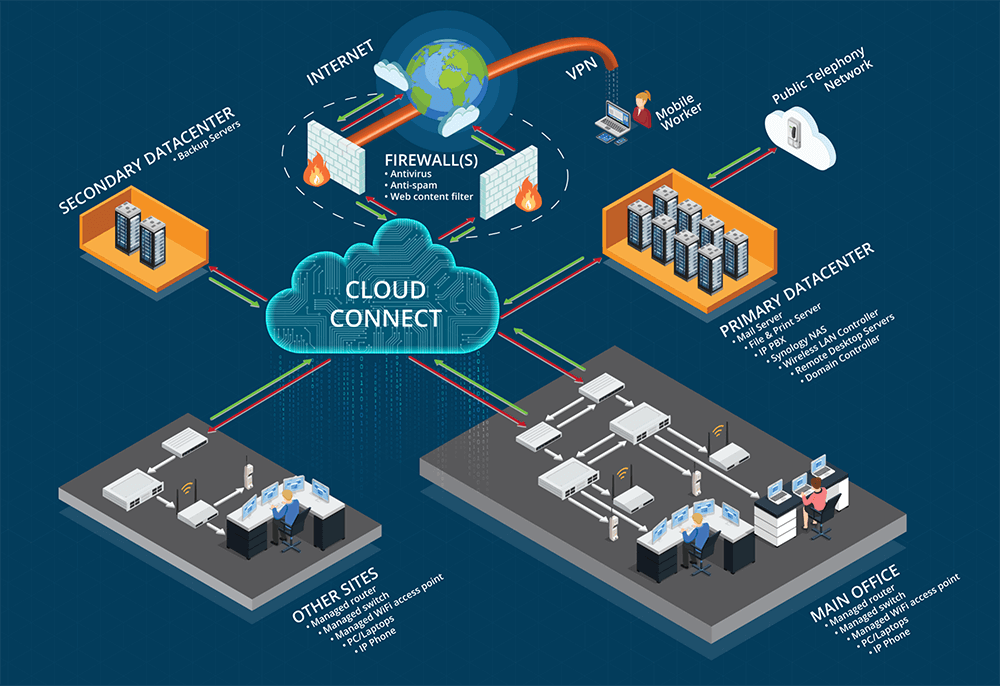
A firewall is the first line of defense for your network against intruders. It secures your network from all kinds of malicious traffic. Traditional setup involves a firewall on customer premises. ITAF’s cloud-first approach provides a cloud firewall. This way the customers can have all their different premises secured with one firewall or one firewall cluster. This is one part of ITAF Cloud services that are scaling up your business performance.
7# Security Awareness
IT Security must be layered so that threats are prevented on all levels of your organization. It is important to educate employees so they can understand the network and host-based threats, the importance of creating strong passwords, recognizing malicious emails, and taking precautions steps to save your company data. That is why ITAF as a security partner can organize security awareness training for your employees or targeted management so that every part of your organization is aware of ways they can protect your data. Our approach contains of continuous training in bite size learning portions, and through phishing simulations.
Contact ITAF
ITAF offers a holistic approach to IT security for small and middle enterprises. From security patching, mail protection, intrusion detection systems, firewalls, IT audits, and your employee education, ITAF can provide you with a complete set of IT security services. Contact ITAF to outsource your data security to IT experts.