
Urgency of Cyber threat Protection in Belgium
In recent years, Belgium has experienced a significant rise in cyber threats, with phishing attacks
Securely host your applications and data in the cloud.
READ MORE
Streamline communication with IP telephony and videoconferencing systems.
READ MORE
Empower your digital transformation with essential tools and licenses.
READ MORE
Secure internet connections, Cloud networks and private WAN.
READ MORE
Professional end-user hardware and software.
READ MORE
Protect your business data and IT infrastructure.
READ MORE
Get efficient IT support and consulting services.
READ MORE
Professional and experienced on-site IT support.
READ MORE
Ensure your IT system is running smoothly and securely.
READ MORE

In recent years, Belgium has experienced a significant rise in cyber threats, with phishing attacks

Cyber threats are becoming more and more complex and frequent. It’s no longer enough for
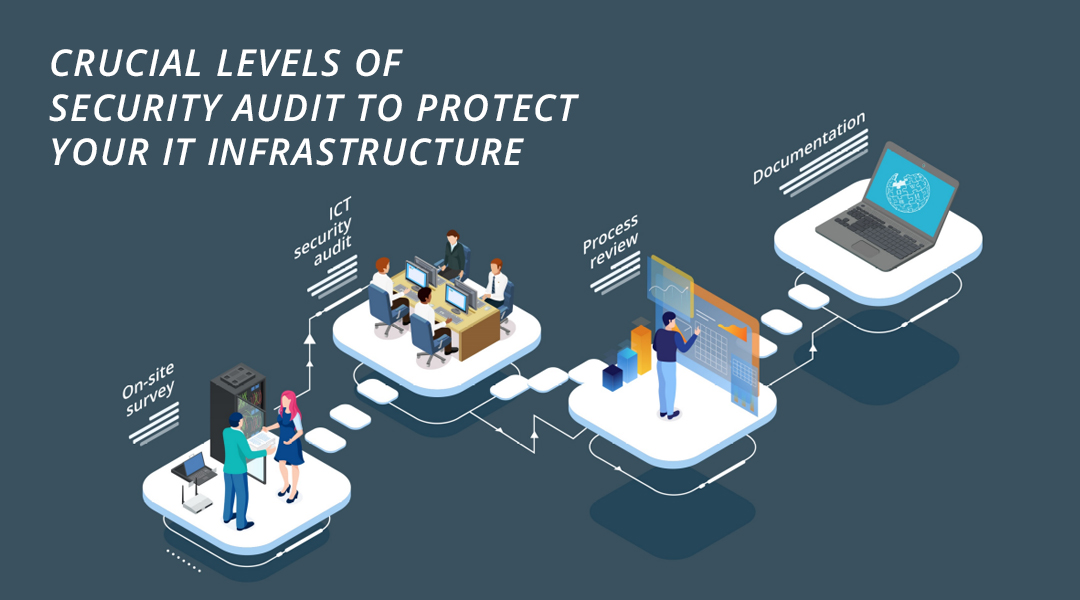
Do you know how secure your IT infrastructure is? These days, due to global uncertainties,

Email protection is commonly the most neglected level of IT security protection. Most businesses forget
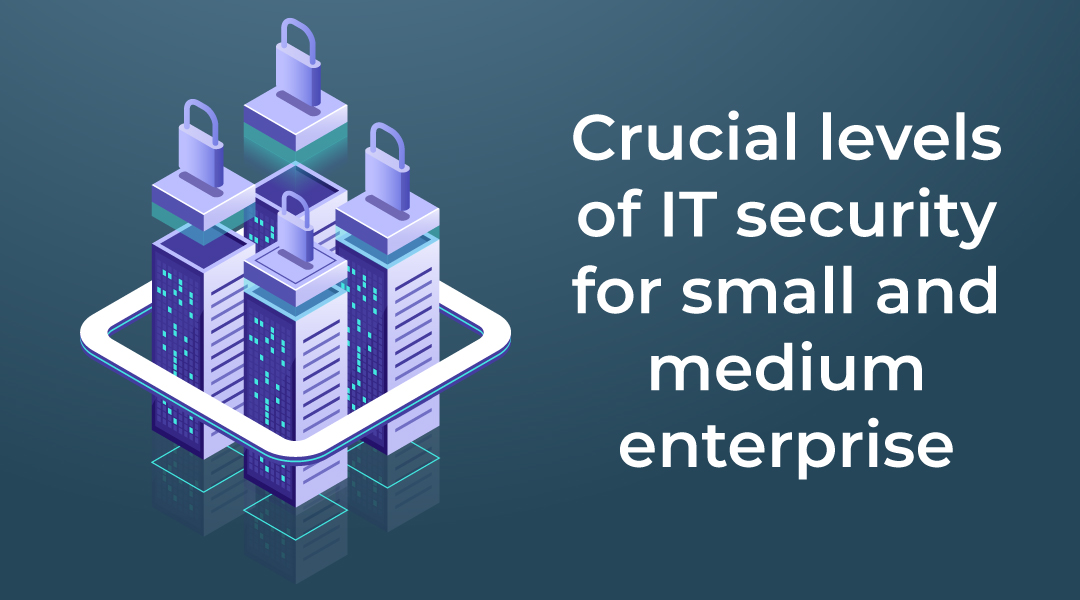
With business growth, IT security takes a pivotal role in protecting your data, infrastructure, and
Security patching as a service today, is still one of the most important parts of

Humans are the weakest link in the cyber security chain. Most of the cyber security
Today it is common to see people use multiple devices for both work and personal
For many companies, the way of working and organization has changed due to Covid-19. As
Need help?